4. Exploiting open ports
Introduction
While we manually explore the results from our subdomain takeover, it's always good to have some automatic scans running, and since i run mine on a VPS (See chapter 98. Using a VPS) I can run some pretty big scans and have them running for a while during my exploration of the targets. For this reason i usually skip to portscanning with nmap and the -sC and -sV flags (more on their meaning later) enabled all of the time. I know that some of us have to hack on a litteral potato though so i will start with the most basic portscans and move on from there.
How do we do it?
To exploit an open port, we first have to know what ports are open and what is running on that port. To do this we have a tool called Nmap, This tool is essential in any pentesters tool belt in my opinion.
We can take two strategies when it comes to an nmap scan, we can either scan every target individually and have a look at the results or we can try to scan the entire list of subdomains we have found at ones. If you already know nmap a little bit you might be used to working with ip adresses but domains do resolve to an ip adress as well, which in turn we can do a portscan on.
We will desribe both techniques since nmap can work with a list as well.
Scanning a list;
nmap -iL list-of-ips.txt -oA scan
Where the -iL stands for input list
And the -oA for output in all formats
Or a single target;
nmap xx.xx.xx.xx This will scan for the default top 1000 ports but there are 65554 ports possible and that's just in UDP, there's also TCP left so if you want to do a more intense scan that's also possible though i do not recommend doing this on a list of URLs since it can take an extremely long time to complete.
nmap xx.xx.xx.xx -p-
for all the ports
nmap xx.xx.xx.xx -sT
for a TCP scan
nmap xx.xx.xx.xx -sT -p-
for all TCP ports
nmap xx.xx.xx.xx -sS
For a TCP syn scan
https://www.youtube.com/watch?v=UHvuH07BQ6w for more infoThe results of this should be a list of subdomains of which we know what ports are open and what not. We can then let nmap automate even more of our work and check for banners for those ports and even execute certain scripts to test for vulnerabilities where possible, though these scripts are ofcourse limited in their capacity.
nmap xx.xx.xx.xx -p 80,81,22,443 -sC -sV
-p will only scan these ports
-sC Will execute the default scripts on those ports
-sV will grab the banners to show the version numbersIf we throw all this together and want to run this on a list of a subdomains and we don't mind how long it runs we can execute the following command.
nmap -iL list.txt -p- -sC -sV
Scan all the UDP ports with banner grabbing
and default scripts from the list list.txtThe results
This will leave you with a list of subdomains, their open ports and if the banner grabbing was succesfull, what is running on that port and the version number possibly. This will allow us to do an exciting night of digging the exploit-db to see if those software versions are vulnerable.
https://www.exploit-db.com/search
We can set some pretty deep options with some elaborate settings in the exploit-db's search fields as seen on the screenshot below.
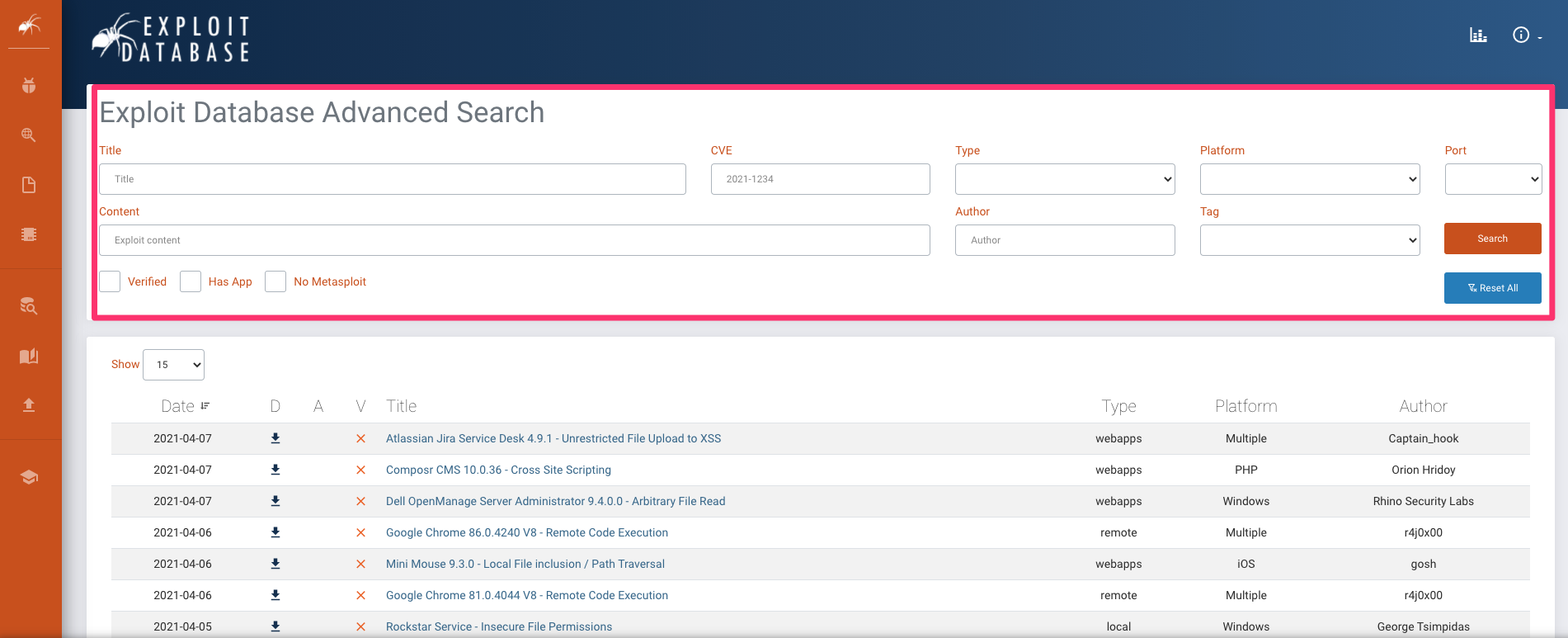
If exploit-db doesn't offer any consolidation there's always google. I usually enter a very straight forward search query 'exploit jira xx.xx' for example. If i find a trace i might have another trail to investigate in exploit-db. I Keep returning there because i know that every exploit in there has a PoC i can use the prove my impact if need be. Remember that you HAVE to be able to demonstrate impact in a proper PoC! No PoC = No Impact = No Issue = No bounty for you and you don't want to let that hard work go to waste.
Where we go from here can vary wildly and is outside of the scope of this course.