A. Vulnerability scanning
What is it?
When we talk about vulnerability scanning, we are talking about scanning our list of domains that we have found up to this point with certain tools that will look for vulnerabilities. Usually the tools themselves will do this by sending out a request and seeing if the response contains all the values that are expected. These test sequences differ per tool and more is not always better.
As with anything, the bigger your list of vulnerabilities, the more time your scan will need to complete for every subdomain from our list. This does not mean much if we have a list that's a few hundred of even a few thousand entries big but this small delay multiplies ofcourse and can grow quite large. After all if we think about it, a 1 second delay may not seem like much but if every target takes 1 second longer and we have 10 000 targets, that's 10 000 seconds or over 2 hours of your valuable time gone.
How do we do it?
We can run several tools such as nikto or nuclei here, my weapon of choice is nuclei because this tool works with templates. These templates are very easy to create for yourself as they are basically yaml files with unique points to nuclei which we will over.
https://github.com/projectdiscovery/nuclei
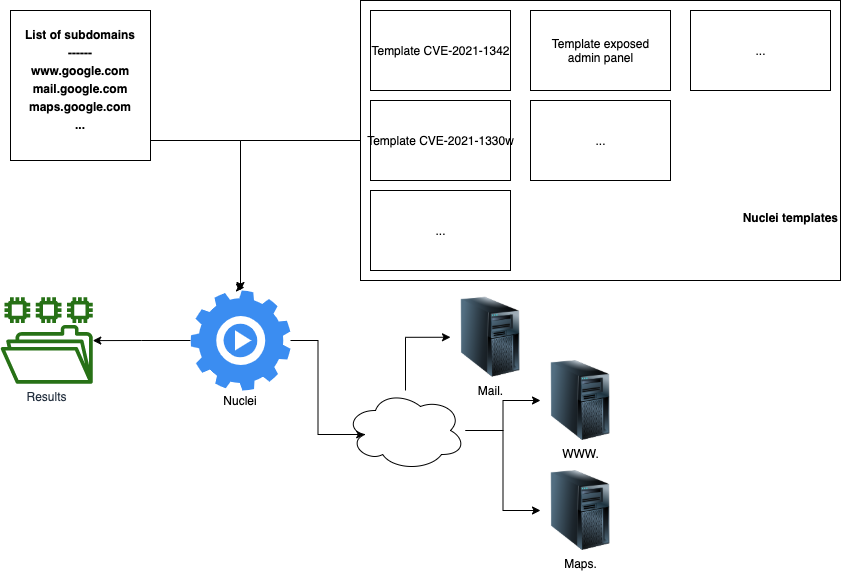
Now the trick is not going to lie in executing already existing templates, though they are pretty useful. We just have to realise that if we neglect to write new templates and only run the default templates, that we are neglecting a big part of what makes nuclei so good. Being able to write and run our own templates is a bliss and it means we can get a competative edge since we will be scanning much deeper than the default templates and if our template turns out to be good, we can commit it to the templates repository so that the whole community can benefit from your work.
Templates
https://github.com/projectdiscovery/nuclei-templates
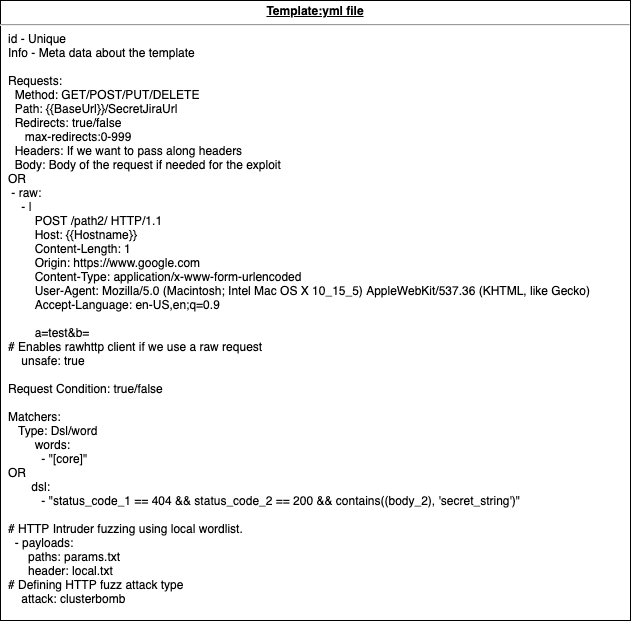
All of this seems very logical and i promise you that it's not as hard as it may seem. Let's have a look at some existing templates to see what they entail.
id: CVE-2005-2428
info:
name: CVE-2005-2428
author: CasperGN
severity: medium
tags: cve,cve2005
requests:
- method: GET
path:
- "{{BaseURL}}/names.nsf/People?OpenView"
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: regex
name: domino-username
regex:
- '(<a href\=\"/names\.nsf/[0-9a-z\/]+\?OpenDocument)'
part: bodyIn our first example we can see CVE-2005-2428 being described. In this CVE, we make a GET request to "{{BaseURL}}/names.nsf/People?OpenView". It will then check if the status code coming back is 200 AND if the body contains a value matching the regex '(<a href\=\"/names\.nsf/[0-9a-z\/]+\?OpenDocument)'.
Lotus Domino R5 and R6 WebMail, with "Generate HTML for all fields" enabled, stores sensitive data from names.nsf in hidden form fields, which allows remote attackers to read the HTML source to obtain sensitive information such as the password hash in the HTTPPassword field.
This regex will try and see if it can find links with that sensitive information enabled.
id: CVE-2021-3378
info:
name: FortiLogger Unauthenticated Arbitrary File Upload
author: dwisiswant0
severity: critical
reference: https://erberkan.github.io/2021/cve-2021-3378/
description: |
This template detects an unauthenticated arbitrary file upload
via insecure POST request. It has been tested on version 4.4.2.2 in
Windows 10 Enterprise.
tags: cve,cve2021,fortilogger,fortigate,fortinet
requests:
- raw:
- |
POST /Config/SaveUploadedHotspotLogoFile HTTP/1.1
Host: {{Hostname}}
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarySHHbUsfCoxlX1bpS
Accept: application/json
Referer: {{BaseURL}}
Connection: close
X-Requested-With: XMLHttpRequest
------WebKitFormBoundarySHHbUsfCoxlX1bpS
Content-Disposition: form-data; name="file"; filename="poc.txt"
Content-Type: image/png
POC_TEST
------WebKitFormBoundarySHHbUsfCoxlX1bpS
- |
GET /Assets/temp/hotspot/img/logohotspot.txt HTTP/1.1
Host: {{Hostname}}
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: word
words:
- "POC_TEST"
part: body
- type: word
words:
- "text/plain"
- "ASP.NET"
condition: and
part: headerThe above CVE will demonstrate a raw request which will check the resulting status code and body and even the headers. The request itself will try to upload a PoC and the matchers will look for that PoC afterwards.
id: active-admin-exposure
info:
name: ActiveAdmin Admin Dasboard Exposure
author: pdteam
severity: info
tags: panel
requests:
- method: GET
path:
- '{{BaseURL}}/admin/login'
matchers:
- type: word
words:
- "active_admin_content"
- "active_admin-"
condition: andAs we can see from the above template, we don't just have to scan for CVE's but can automate the scanning of a lot more.
If we want to combine several templates, we can combine them in a workflow file.
id: micro-focus-workflow
info:
name: Micro Focus Checks
author: dwisiswant0
description: A simple workflow that runs all Micro Focus related nuclei templates on a given target.
workflows:
- template: default-logins/UCMDB/micro-focus-ucmdb-default-credentials.yaml
- template: cves/2020/CVE-2020-11853.yaml
- template: cves/2020/CVE-2020-11854.yaml